Recently, I encountered an issue where I was unable to access the vCenter web interface in my Test-Lab, after restoring to a pretty old Snapshot. Upon attempting to log in, I was met with the errors “No healthy upstream” and “503 – Service Not Available” on the management interface. This blog post outlines how I debugged and resolved this issue, which turned out to be caused by an expired certificate.
Initial Debugging Steps
When faced with the above errors, the first step is to identify the root cause. Here are the steps I followed to debug the issue:
Step 1: Check vCenter Services
Using SSH access to the vCenter Server Appliance (VCSA), I verified the status of all vCenter services:
service-control --statusI found that some services were not running or were in a degraded state.
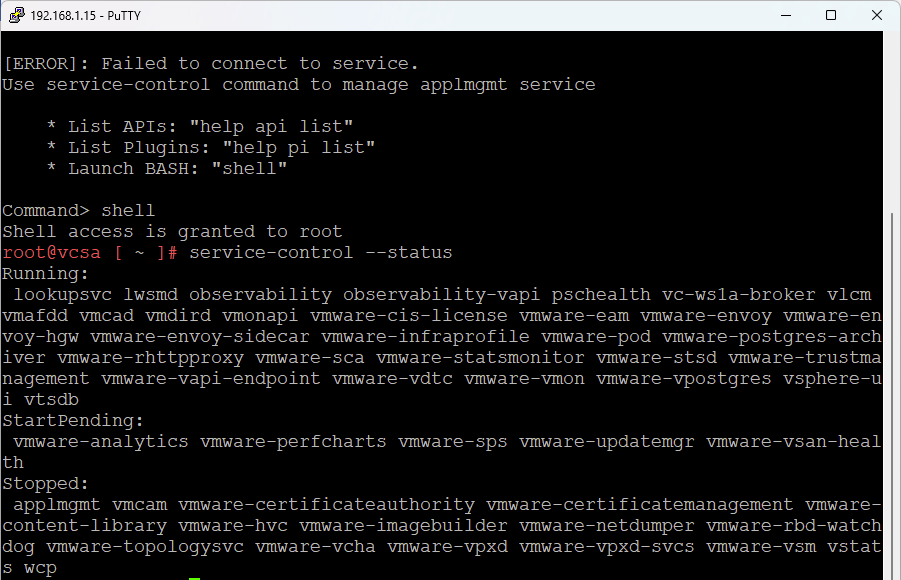
Step 2: Review Logs
Logs are an essential resource for debugging. I examined the following logs for clues:
- vCenter server logs:
tail -f /var/log/vmware/vpxd/vpxd.log- Appliance management logs:
tail -f /var/log/vmware/applmgmt/applmgmt.logIn the applmgmt.log, I found entries indicating issues with expired certificates:
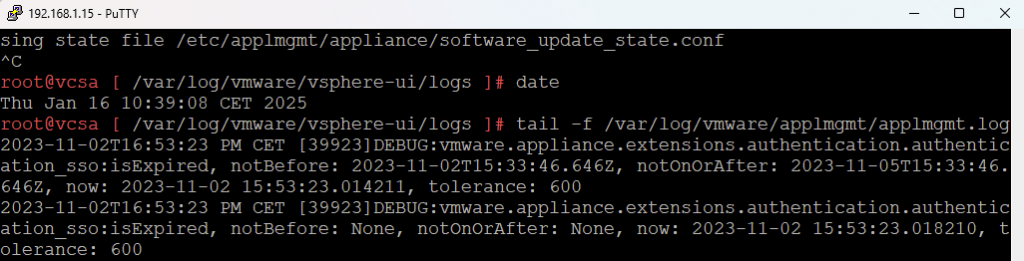
DEBUG:vmware.appliance.extensions.authentication.authentication_sso:isExpired, notBefore: 2023-11-02T15:33:46.646Z, notOnOrAfter: 2023-11-05T15:33:46.646Z, now: 2023-11-02 15:53:23.014211Step 3: Check All Certificates on VCSA
Using the following command, I listed and inspected all the certificates on the VCSA:
for store in $(/usr/lib/vmware-vmafd/bin/vecs-cli store list | grep -v TRUSTED_ROOT_CRLS); do \
echo "[*] Store :" $store; \
/usr/lib/vmware-vmafd/bin/vecs-cli entry list --store $store --text | grep -ie "Alias" -ie "Not After"; \
done;This command iterates through all certificate stores and lists details for each certificate, helping identify any that have expired. I’ve noticed some certificates were expired, so I have to regenerate them in order to be able to access vCenter again.
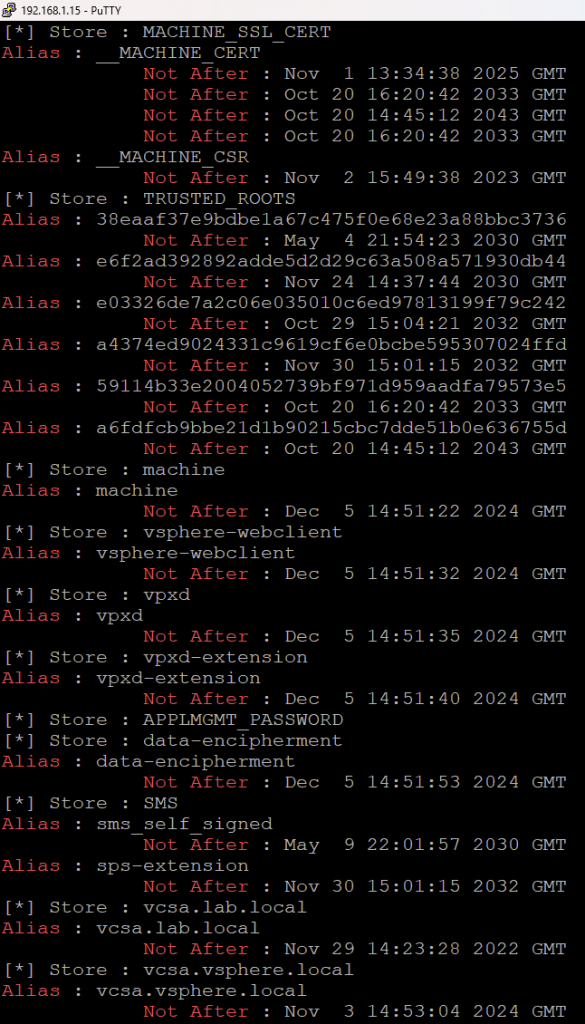
Generating and Applying a Self-Signed Certificate
To resolve the issue, I replaced the expired certificates with new self-signed certificates. Here are the steps I followed:
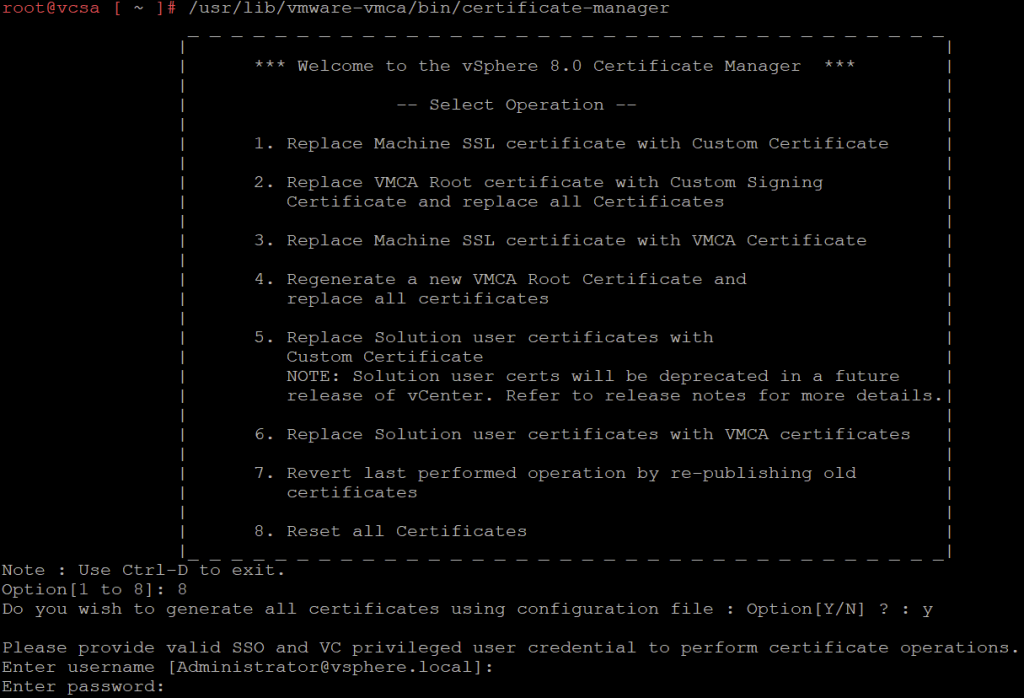
Step 1: Access the Certificate Manager
Start Certificate Manager using this command
/usr/lib/vmware-vmca/bin/certificate-managerStep 2: Select the Reset All Certificates Option
From the menu, select Option 8:
Reset all CertificatesStep 3: Generate the Certificate
The Certificate Manager tool prompts you to confirm that you want to generate all the certificates.
Step 4: Provide Administrator Credentials
Enter the SSO administrator username (e.g., administrator@vsphere.local) and password.
After entering al the details for the certificate, I had to confirm if I want to regenerate Root Certificate and replace all certificates using VMCA.
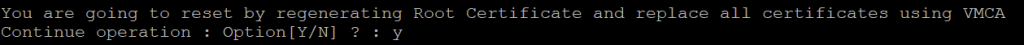
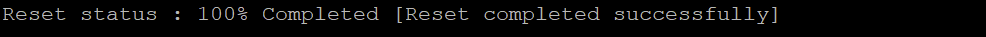
The certificates were successfully replaced and the services were restarted.
Verifying the Fix
After completing the steps above, I verified that the vCenter web interface was accessible:
- Open a browser and navigate to the vCenter URL (e.g.,
https://<vcenter-fqdn>). - Check the SSL certificate details to confirm the issuer and validity period.
- Log in to ensure all services are operational.
Lessons Learned
While this issue occurred in a lab environment and was not critical for me, as I had restored an old snapshot and was aware this might happen, it is important to implement mechanisms to avoid such problems in production environments. Here are some best practices:
This issue highlighted the importance of monitoring and managing certificates in vSphere environments. To avoid similar problems in the future:
- Regularly check certificate expiration dates.
- Set up alerts for certificate renewal in your monitoring tools.
- Consider using custom certificates if required by your organization’s policies.
By following these steps, I was able to restore access to the vCenter and ensure uninterrupted management of the virtual infrastructure. If you encounter similar issues, I hope this guide helps you resolve them efficiently.
Sources
Here are some resources that were helpful during the process:
